Difference between revisions of "Spacenet"
m (wait, I didn't do anything on the new spacenet, that was stuiterveer :P) |
m (Trying to list properties (once) Not sure about 802.11ac value, though) |
||
| Line 183: | Line 183: | ||
== Available SSID's == | == Available SSID's == | ||
| + | |||
| + | We also have some materials for it (TODO: not an exact list): | ||
| + | * [[WLAN::spacenet;5GHz;802.11ac;Spacenet]] | ||
| + | * [[WLAN::spacenet_legacy;2.4GHz;802.11g;Spacenet for hardware that does not have a 5GHz WLAN interface]] | ||
| + | * [[WLAN::ackspacewifi;2.4GHz;802.11g;More or less reserved for IoT and the like. Usage is discouraged]] | ||
| + | |||
| + | {{#subobject: | ||
| + | |SSID=test | ||
| + | |Band=2.4GHz | ||
| + | |IEEE=802.11g | ||
| + | |Text=Fake! | ||
| + | }} | ||
| + | |||
| + | {{#ask: [[WLAN:: ~spacenet*; ?; ? ; ?]] }} | ||
| + | |||
{| class="wikitable" | {| class="wikitable" | ||
! scope="col" | SSID | ! scope="col" | SSID | ||
Revision as of 11:18, 19 April 2019
| Project: Spacenet | |
|---|---|
| Featured: | No |
| State | Completed |
| Members | Xopr, Stuiterveer |
| GitHub | No GitHub project defined. Add your project here. |
| Description | Connect to an encrypted accesspoint using your own credentials in every hackerspace |
| Picture | |
| |
Contents
We haz spacenet.
Certificate
the certificate, as from /etc/freeradius/certs/server.pem
-----BEGIN CERTIFICATE----- MIIDBjCCAe6gAwIBAgIUPNOYqWrcqQkZt63WzVOz2mE21igwDQYJKoZIhvcNAQEL BQAwIzEhMB8GA1UEAwwYdi0xLjI4MzQ1LnZwc2NvbnRyb2wubmV0MB4XDTIxMDMx MzIyNDgyMloXDTMxMDMxMTIyNDgyMlowIzEhMB8GA1UEAwwYdi0xLjI4MzQ1LnZw c2NvbnRyb2wubmV0MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAyiVB khJJqglAfRdPJr0nVspZdm9DoCD0XidkOW1Tj7Q1pfQHLs0lGA/aIQqofw8W+tkR BjJNb0mOprhltAFW68Y/qgeGWuOzyp8xrZGP6jA1xQRPFbUUCV2ZG6avwJUTYZoF 1TwCo0UpsCQRmpjMgMfBdlBKKaqO2kr2q7SbT/QnDX04+E7B1cnfdfCSobOBiitD 6HX/D19l6bryriMhaz42SWd6CbpRY1Qac7bCNbJ0Re5cyjvkJvojnDp12MMMoyVg QeTxQ4V+Z8HOmzthtFZNGFnLn0YAVIGLDBwhWodX8p51D+DPY5uIR6cR3Eiphd5h 1jpmA5IYB+Dw4X0W9wIDAQABozIwMDAJBgNVHRMEAjAAMCMGA1UdEQQcMBqCGHYt MS4yODM0NS52cHNjb250cm9sLm5ldDANBgkqhkiG9w0BAQsFAAOCAQEAngk8xf8R k6LTohmNbViDtggdSBhHwJRvGytVcsPNgyP/TUW2fPhVOMSg6iU4U95U1CEMXfIG DaeNfRg9bDqfGzvtK/KTET7kxLM7IzCHHuHEd4t6N0wlArTIZHFROLQ9pqAV7BIw nlurPVxOYVEb9PPtEYk+qcJRlB7lamTOyvMecjiFV1BXjpmO4nMeQ5vu8gT8hi0y xfyNEDZSYm1UCWqc/mFuOIbpOHzaNngh/pfVu30kSEMUS4L0wLP7Ju/QnOOy/jKF wxRlSPlHvDV910rlZlbi6G0XgH8MpIrPFhJnvbXUME0p0524iPsCUyJIh9X2Te07 NApMIN43u3sTJA== -----END CERTIFICATE-----
Connecting
Go to the chapter of your operating system below.
Linux
Copy & Paste the certificate above into a file and name it ackspace.pem
Put it in your own home folder.
Linux WIFI settings:
| field | setting |
|---|---|
| Network name | spacenet and/or spacenet_legacy |
| Wireless security | WPA & WPA2 Enterprise |
| Authentication | Tunneled TLS (TTLS), or PEAP |
| Anonymous identity | anonymous@ackspace.nl |
| CA certificate | ackspace.pem |
| PEAP version (optional) | automatic Inner |
| Inner authentication | MSCHAPv2 (or PAP without a certificate) |
| Username | <user>@ackspace.nl |
| Password | you should know this |
Windows 7
<Da_Syntax>
- Windows 7 uses ntlm v2 and will fail trying to authenticate with the router.
- In order to fix this run (win+'r') "secpol.msc" and do the following:
- Open "Local Policies" > "Security Options" > "Network Security: LAN Manager authentication level"
- and select "Send LM & NTLM - use NTLMv2 session security if negotiated" from the dropdown box
- Press Ok, reboot ... profit!!
</Da_Syntax>
Windows 7 will either support EAP-MSCHAPv2 (username/password) or EAP-TLS (certificates) out-of-the-box.
You should manually create a wireless network under "Manage wireless networks".
Depending on the configuration of your home-RADIUS you should either choose EAP-MSCHAPv2 or EAP-TLS.
EAP-MSCHAPv2
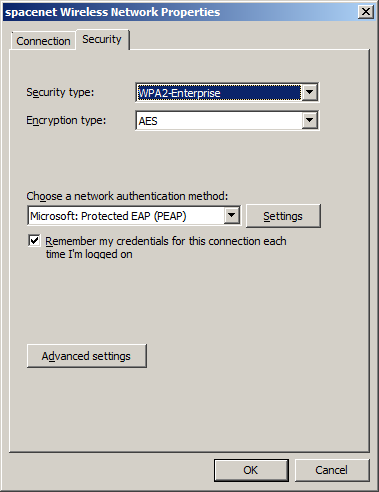
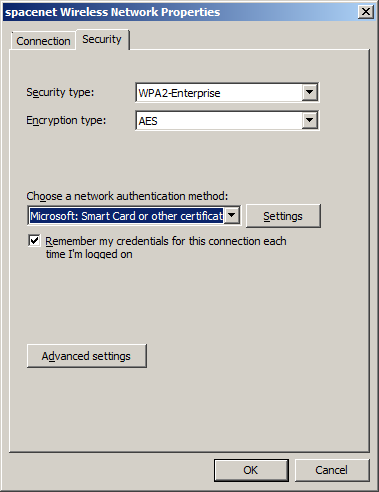
- SSID: spacenet
- Security type: WPA2-Enterprise
- Encryption type: AES
- Authentication: Microsoft: Protected EAP (PEAP)
DO NOT USE CERTIFICATE WITH WINDOWS.
DO NOT ENTER RADIUS NAME OR IP.
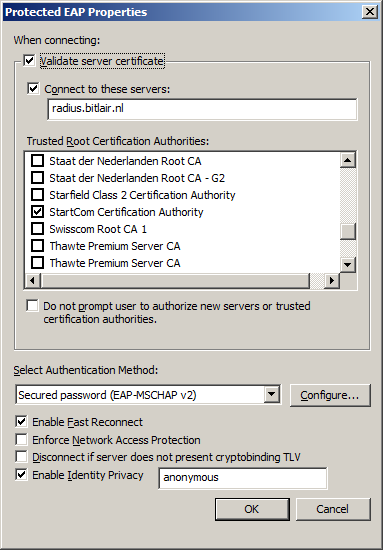
- Validate server certificate (good practice)
- Connect to these servers: common-name of the certificate installed on your RADIUS server
- Trusted root certification authorities: select the CA which signed the certificate installed on your RADIUS server
- Authentication method: secured passwords (EAP-MSCHAP v2)
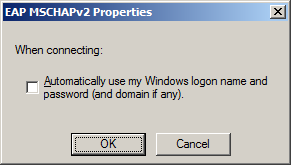
- Do NOT use windows logon name and password (will probably not work for you)
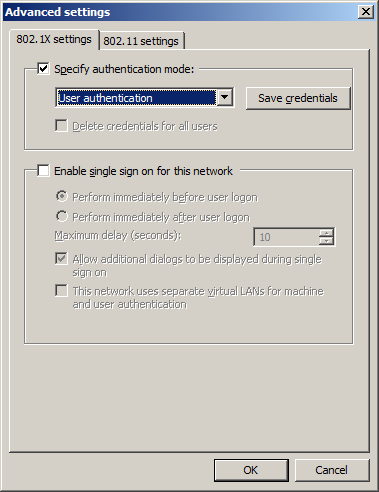
- Use user authentication
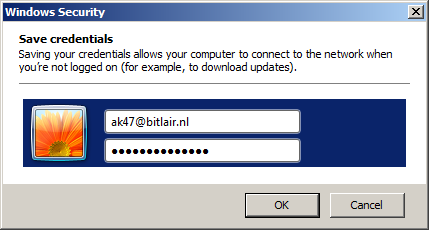
- Save credentials: user@ackspace.nl with your password
EAP-TLS
- Make sure your device has a client certificate issued by your PKI
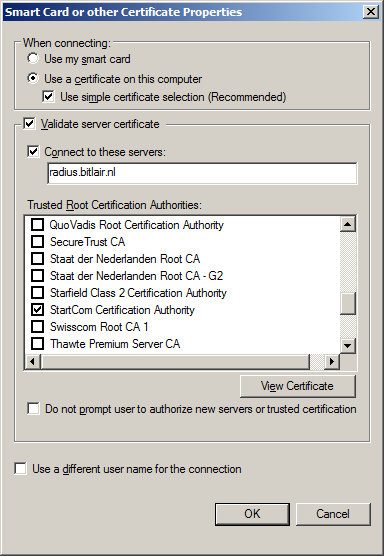
- SSID: spacenet
- Security type: WPA2-Enterprise
- Encryption type: AES
- Authentication: Microsoft: Smart Card or other certificate
- Validate server certificate (good practice)
- Connect to these servers: common-name of the certificate installed on your RADIUS server
- Trusted root certification authorities: select the CA which signed the certificate installed on your RADIUS server
iOS (iPhone and iPad)
just use your username and password an accept the certificate.
SailfishOS (Jolla)
For ease of typing on a big keyboard, make sure you have Developer mode and Remote connection enabled. Connect to the phone using SSH, gain root, and create the server certificate.
ssh nemo@<ip> su-devel vi /etc/ssl/certs/ACKspace.pem
press i, paste the certificate info, press Esc, :wq followed by enter
Create the WPA2 enterprise config:
vi /var/lib/connman/wifi_spacenet.config
press i and paste the following text:
[service_spacenet] Type=wifi Name=spacenet EAP=peap CACertFile=/etc/ssl/certs/ACKspace.pem Phase2=MSCHAPV2 Identity=<user>@ackspace.nl Passphrase=<your password>
Logout, disable wifi, enable it again. Go to System, WLAN, connect to internet, and tap WLAN spacenet shouldbe in the list; tap to connect.
How to register
To use Spacenet, ACKspace needs to store your plain text username (the part before @ackspace.nl) and an NTLM hash of your password you wish to use. If you use the hashes generator, make sure you enter your password without username or domain etc.
Contact PsychiC, Vicarious, Xopr or Stuiterveer if you'd wish to register.
Info for freeradius admin
edit /etc/freeradius/users Add either one of lines
- noobuser Cleartext-Password := "foobar123"
- leetuser NT-Password := "FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF"
NTLM hash generator
(note that there is no roundtrip involved, hash is generated client-side using utf8-to-utf16 little endian and md4 hash)
NTLM.py
import hashlib,binascii
passwd = '$password'
print 'NTLM hash is', binascii.hexlify(hashlib.new('md4', passwd.encode('utf-16le')).digest())
# OR use
import smbpasswd # via [apt-get install | yum install] python-smbpasswd
passwd = '$password'
print 'NTLM hash is', smbpasswd.nthash(passwd)
Available SSID's
We also have some materials for it (TODO: not an exact list):
- spacenet;5GHz;802.11ac;Spacenet
- spacenet_legacy;2.4GHz;802.11g;Spacenet for hardware that does not have a 5GHz WLAN interface
- ackspacewifi;2.4GHz;802.11g;More or less reserved for IoT and the like. Usage is discouraged
| SSID | description |
|---|---|
| spacenet | spacenet |
| ackspacewifi | Needs WPA2 key (ask a participant) |